Any Sensor, Best Weapon: IBCS’ 2025 Breakout Moment
October 2025 marked a turning point for the Integrated Battle Command System. Soldier-run tests, Poland’s live-fire, and Guam’s architecture show air and missile defense becoming software-defined, plug-and-fight, and coalition-ready.

The moment air defense became software-defined
On October 2, 2025, at White Sands Missile Range, soldiers used the Integrated Battle Command System to detect, track, and down two maneuvering cruise-missile targets with two first-shot intercepts. The U.S. Army published the result a few days later and did not bury the lede: this was not a lab vignette, it was a soldier-run engagement in a contested environment that validated the heart of the “any sensor, best weapon” idea in the Army report on White Sands test. Two weeks earlier, in Ustka, the Republic of Poland conducted the first international live-fire of an Integrated Battle Command System network, an operational demonstration that advanced Poland toward full capability and proved that this architecture works outside U.S. formations, as captured in the Army note on Poland live-fire.
Those two bookend events, paired with the U.S. push to make Guam’s layered defense revolve around the same software core, mark a genuine inflection. Air and missile defense is shifting from platform-centric to software-defined. Sensors and shooters are no longer locked in fixed pairs. Instead they plug into a network that assembles a composite picture and matches the best shooter to a threat in real time. This mirrors the broader kill web shift described in SDA’s LEO constellation goes live.
This is not a marketing slogan. It is a design change with operational consequences: faster engagements, more resilient networks, better use of scarce interceptors, and a path for allies to join the fight without replacing everything they already own.
From stovepipes to software
For decades, ground-based air defense worked like this: a radar detected, a collocated control station decided, and a launcher nearby fired. The pieces were vertically integrated. If you swapped the radar, you usually had to swap everything else. That tight coupling simplified test and training, but it created brittle seams. If a radar went down or terrain masked it, the battery went blind. If the launcher had the right missile but the wrong controller, you could not use it.
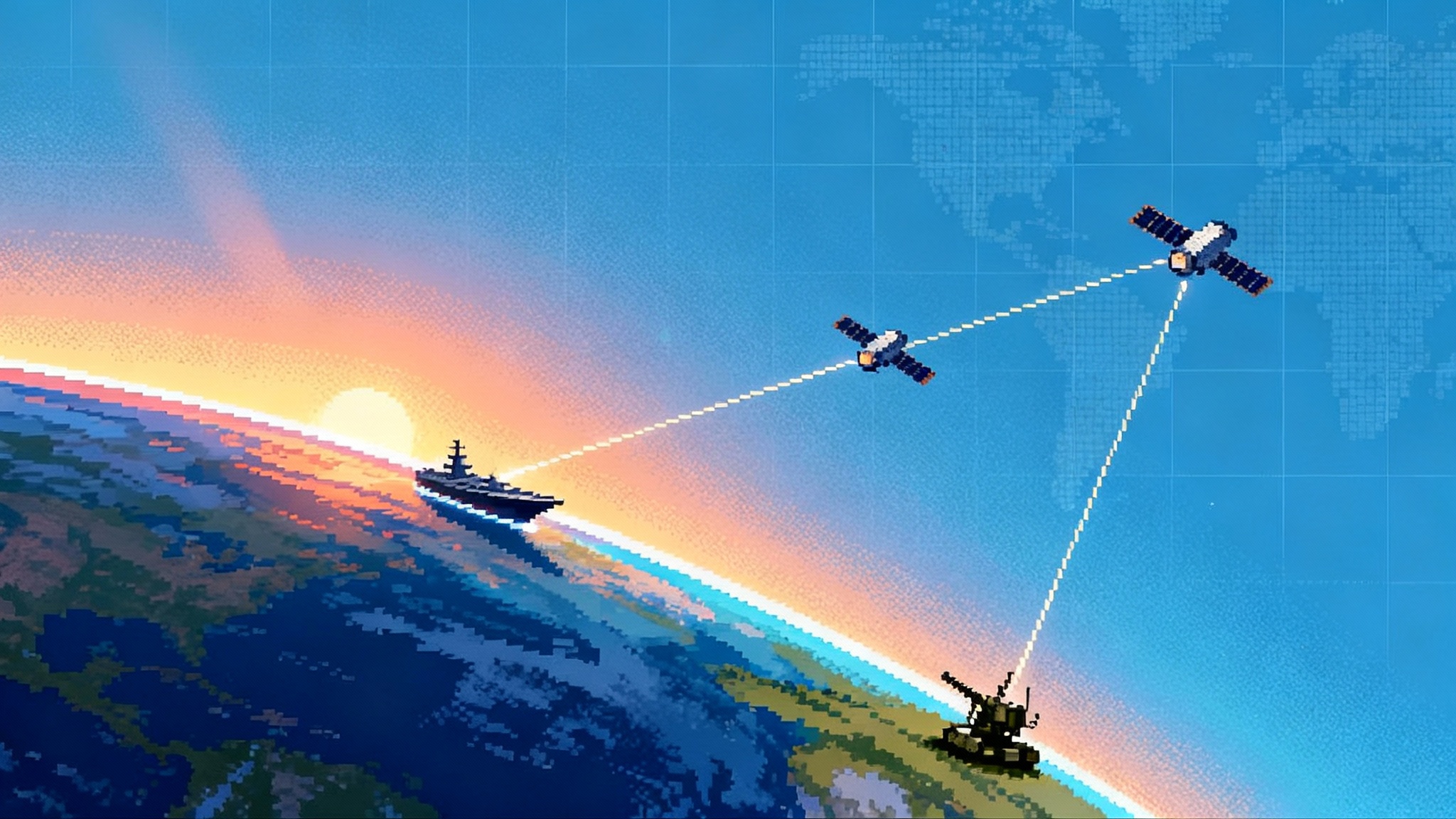
The Integrated Battle Command System breaks those seams. It treats sensors as producers of measurements and shooters as consumers of fire-quality tracks. The software fuses data from diverse radars into a single stable track, calculates which weapon has the reach, look angle, and probability of kill, and then commands the shot. It does this over a distributed fire control network rather than a single cable bundle in one vehicle. The practical effect is simple: any radar can help any launcher, and any launcher can be tasked from anywhere on the network, subject to policy and rules of engagement.
If you have seen a conductor cue sections of an orchestra, you have the right mental picture. The score is the engagement doctrine. The section leaders are the sensors. The instruments are the launchers. The conductor does not play a violin or a trumpet. It ensures each plays at the right time and volume. When a soloist falters, the rest of the ensemble covers so that the music continues.
What changed in 2025
Three threads converged this year to make the shift visible outside specialist circles.
- Proved performance under soldier control. The White Sands event was not a developmental demo. It was part of follow-on operational testing with real units under jamming and deception. Two first-shot kills against maneuvering cruise-missile targets reduce the risk that fusion math or message timing will stall under pressure. That matters because cruise missiles fly low, use clutter to hide, and often maneuver late.
- First allied live-fire inside the architecture. Poland’s live-fire was more than a national milestone. It was proof that an ally can join a software-defined network and execute with operational realism. Poland’s modernization blends existing Patriot launchers and interceptors with new radars and command nodes. The glue is software. That is fundamentally different from buying a single monolithic system.
- Guam’s pivot to integration. Guam’s defense plan is not a single site with a single radar. It is a layered architecture that must survive saturation raids, electronic attack, and complex trajectories. The U.S. Army is organizing its land-based layer around the Integrated Battle Command System so that Patriot launchers, the new Lower Tier Air and Missile Defense Sensor, and the Indirect Fire Protection Capability can cooperate with Terminal High Altitude Area Defense batteries and share cues with naval Aegis assets. This choice reflects a lesson the services have learned the hard way: resilience comes from diversity stitched together by software, not from making one box perfect.
How plug-and-fight actually works
The phrase “plug-and-fight” sounds like a slogan until you see the control-room view. Here is a concrete example.
- A low-flying cruise missile pops over the horizon, too low for a single radar to hold cleanly. A forward Sentinel radar paints the first faint return. A different radar, the Lower Tier Air and Missile Defense Sensor, sees lobe-after-lobe as the target weaves through clutter. The network fuses those fragments into a single track whose quality is better than either source alone.
- The software checks range rings, look angles, and time-to-go for every connected launcher. A Patriot launcher on a ridgeline has a clear arc but is farther away. An Indirect Fire Protection Capability launcher is closer, with a different interceptor profile. The algorithm weighs the geometry and doctrine and recommends a shooter, then transmits a fire-quality engagement order to the chosen launcher.
- The launch authorization and the shot proceed without moving a single vehicle. The radar that started the track could be 30 kilometers from the launcher that executes the kill. If any node goes dark, the track continues from other sensors. If a launcher runs out of interceptors, the system automatically finds another with the right magazine load and firing geometry.
This is why the approach scales. You can add a radar without redesigning the entire battery. You can extend coverage by placing remote launchers in better terrain instead of towing the entire battery onto a hill. You can integrate new effectors as long as they can accept a fire-control message and provide status back to the network.
The joint and coalition mix in plain language
- Patriot and the Lower Tier Air and Missile Defense Sensor. Patriot launchers carry interceptors like the PAC-3 Missile Segment Enhancement, built by Lockheed Martin, while Raytheon produces the new 360-degree sensor that replaces the older Patriot radar. Integration through the command system lets any connected radar contribute to a Patriot shot, and lets Patriot launchers fire based on the best track available, not just their own sensor.
- Terminal High Altitude Area Defense. THAAD is built to engage higher, faster threats. It uses the AN/TPY-2 radar for long-range tracking. Through software bridges, THAAD can contribute measurement data to the network and benefit from composite tracks that reduce ambiguity. The end state is a handoff that looks seamless to the operator even if the sensors come from different services.
- Indirect Fire Protection Capability. IFPC is the Army’s program for defending against cruise missiles, rockets, artillery, mortars, and unmanned systems. It uses a modular launcher that can employ different effectors. As IFPC matures inside the network, commanders get more shot options for short-to-medium range threats without dedicating Patriot missiles to every small target.
- Aegis with Standard Missile 6. The Navy’s Aegis Combat System and SM-6 interceptor extend the envelope at sea and ashore. The practical value of the new approach is that the land network and the naval combat system can share targeting cues at fire-control quality rather than just exchanging chat messages. For context on the land-based use of SM-6, see land Tomahawk and SM-6.
Internationally, Poland is the pathfinder. It shows that allies can plug their legacy and new components into the same engagement logic. Others have compatible parts or are moving that way. The design choice here matters: once allies share the software heartbeat, they do not have to buy identical hardware to fight as one.
Why 2026 to 2028 will move fast
If this is the inflection, the slope of the curve over the next three years matters. Several concrete drivers point to acceleration.
- Mature software baselines. The version that soldiers used in October is not a prototype. It is the result of years of soldier-touch experiments, electronic warfare stress testing, and operational trials. That means field units can adopt it with fewer surprises.
- Production lines are finally aligned. Raytheon’s new radar is in production. Patriot launchers are being delivered with the command system interfaces already baked in. The Army is standing up a Patriot battalion specifically for Guam and updating existing battalions to the new architecture. Every step reduces retrofit friction.
- Allied funding is committed. Poland is already executing. Other European partners that operate Patriot or plan to add complementary systems can join by upgrading software and gateways rather than replacing everything. Budgets that once went to big hardware swaps can partially shift to networked integration and remote launchers.
- The threat is compressing timelines. Drone swarms and low-flying cruise missiles shorten reaction time. Hypersonic glide vehicles complicate midcourse tracking. A software-defined network buys time by shortening the sensor-to-shooter loop and making every radar and launcher more useful, every minute of every day.
The result will look like this by late 2028: more units in Europe and the Indo-Pacific operating with distributed radars and remote launchers, common engagement logic across services, and coalition formations that can exchange fire-quality tracks on day one of an operation. For a related ground view on countering small aerial threats, see counter-drone standard issue in 2025.
The catch: software is a capability and a liability
A network that makes any sensor feed any shooter creates new failure modes that commanders and engineers must address head-on.
- Cyber and zero trust. If software is the center of gravity, it is also the prime target. The network needs enforceable identity for every node, robust key management for coalition partners, and anomaly detection for anything that tries to impersonate a radar or a launcher. This is not a compliance checklist. It is uptime under fire.
- Spectrum combat. The network must live in a jammed world. That means multiple bearers, frequency agility, and the ability to degrade gracefully. Operators need clear playbooks for when to downshift from high-bandwidth fire-control quality to lower-fidelity tracking while still preserving engagement options.
- Magazine depth. The command system can match the best weapon to the threat, but it cannot conjure interceptors. Nations will still need to increase magazine depth for high-demand missiles, add cheaper effectors for lower-end threats, and preposition reloads in ways that sustain distributed launchers.
- Coalition policy and data rights. Plug-and-fight is technical. Plug-and-fight with allies is political and procedural. Who can authorize a shot from whose launcher. What classification applies to fused tracks. How are logs shared for after-action analysis. These are solvable questions, but they need decisions before the exercise, not after the first inbound target.
What leaders should do now
The shift is here. The question is how quickly units can translate it into readiness. There are specific, concrete actions that matter in the next 12 months.
- Map kill-web baselines. Treat your area of responsibility like an electrical plan. Which sensors feed which launchers today. Where are the network single points of failure. Identify the gaps that software cannot cover, like terrain shadows that need a relocated radar or a new mast.
- Pre-certify coalition plugs. If you will operate with a partner, run the cryptographic and interface approvals now, not during the deployment. The paperwork lead time often exceeds the training lead time. Put a named officer in charge and track it like a key performance parameter.
- Train to remote operations. Practice with radars and launchers separated beyond line-of-sight under realistic terrain and jamming. Write tactics for how to reposition remote launchers in hours, not days, and how to maintain them when the command post is miles away.
- Budget for the boring. Fiber spools, power conditioning, spare network radios, and environmental control units do not make headlines. They keep a software-defined architecture alive in the field. Fund them explicitly.
- Expand the effector mix. Use the network to push lower-cost interceptors against easier targets and reserve premium rounds for the hardest problems. This means bringing Indirect Fire Protection Capability into the same daily training loop as Patriot and Terminal High Altitude Area Defense, not treating it as a separate craft.
- Write joint playbooks. A ship’s combat system and a land-based fire control system can now act as one team. That requires shared checklists for engagement authority, battle damage assessment, and link management. Put a ship rider in the land battery and a land rider on the ship during the next exercise and make them co-author the checklist.
The bottom line
October’s first-shot cruise missile kills, Poland’s international live-fire, and Guam’s integration moves are not isolated headlines. Together they confirm that air and missile defense is crossing a line. The decisive element is no longer a single radar or a particular interceptor. It is software that sees the whole sky through many eyes, chooses the best hand to play at that instant, and executes faster than a human could stitch the pieces together.
Because software scales faster than hardware can be designed and built, 2026 to 2028 will favor the organizations that embrace the network mindset now. Units that do will fight with more look angles, more firing options, and more resilience than their order of battle suggests on paper. Nations that delay will keep buying excellent boxes that cannot sing together.
The orchestra has a conductor now. The music will get faster. Those who learn the score will set the tempo.