Dreamforce 2025: Agent Control Planes Go Mainstream
At Dreamforce 2025, Salesforce unveiled Agentforce 3 with a Command Center, Model Context Protocol support, and compliance upgrades. The signal is clear: control planes, not bigger models, will make enterprise agents observable, governable, and interoperable at scale.

The big shift everyone felt at Dreamforce
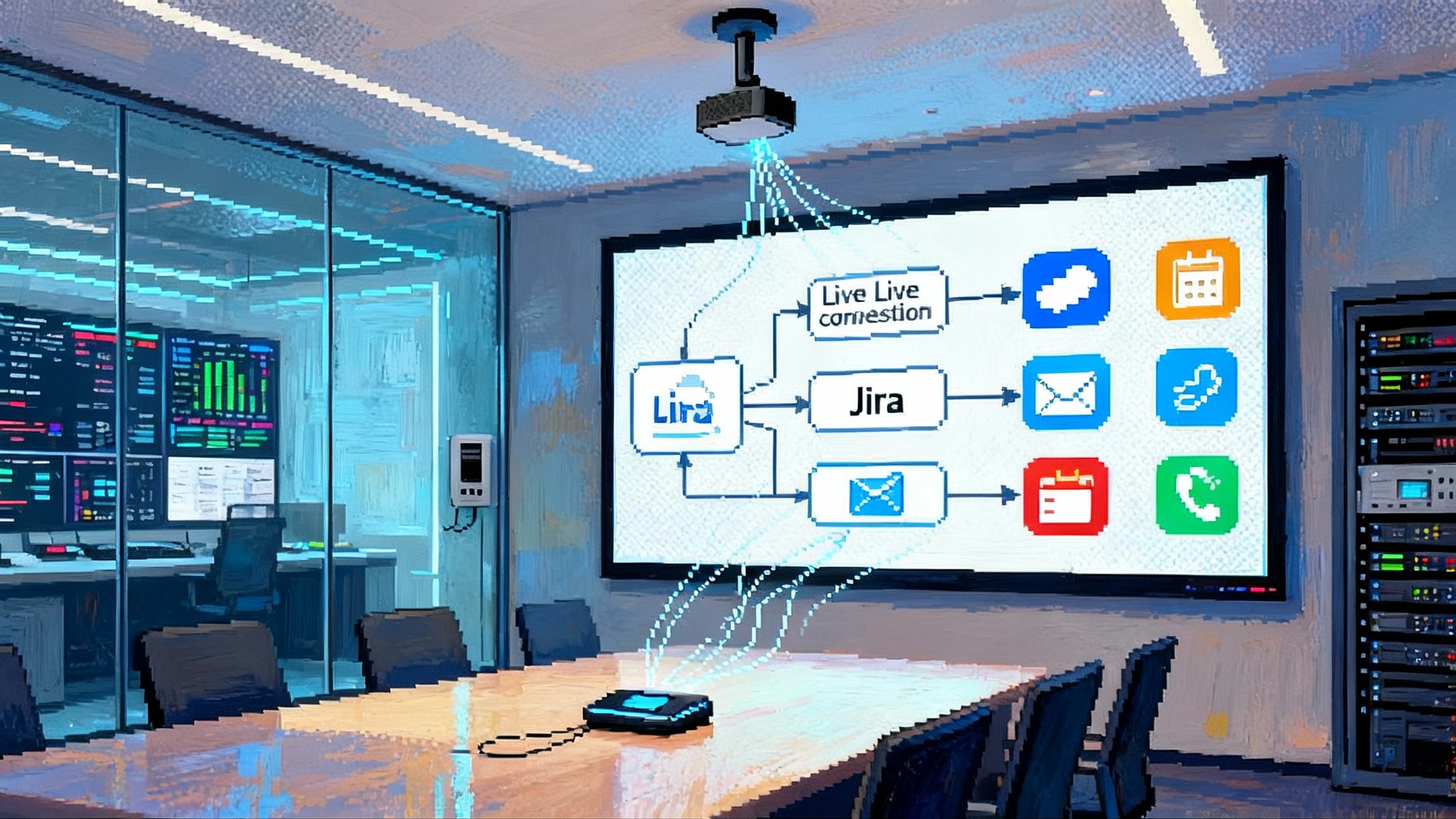
At Dreamforce 2025 the loudest message was not another bigger model or benchmark score. It was control. Salesforce’s new Agentforce 3 put the spotlight on a different competitive layer in artificial intelligence: agent control planes. In its announcement, Salesforce introduced a Command Center with deep observability, native support for the Model Context Protocol, and compliance upgrades including public sector authorization. The headline is simple, and it lands with force: the winners in enterprise AI will be the platforms that make agents observable, governable, and interoperable at scale, not just the ones that claim smarter reasoning. Salesforce’s launch details underscore that point.
Think of an agent control plane like air traffic control for digital labor. Models are the engines, tools are the airports and runways, and the control plane coordinates flight plans, identity checks, telemetry, and safety procedures. Without that layer, you can have fast jets and great airports, yet still get chaos in the sky. Agentforce 3 turned this metaphor into product design, then shipped it to customers who need evidence, not slogans.
What an agent control plane actually is
The phrase agent control plane can sound abstract. Here is a concrete breakdown of what enterprises now expect from this layer:
- Observability: session traces, cost per task, latency by tool call, failure modes, escalation paths, and human handoff moments. Agentforce 3 surfaces these as dashboards and traces rather than anecdotes. It treats agent work like a first class workload that must be measured and tuned.
- Governance: policy checks before tools are called, identity and data boundary enforcement, record of what was accessed and why, and a way to freeze or roll back changes. This is the practical form of trust, not a marketing word.
- Interoperability: native connectors to internal systems and external services, plus a standard so that different vendors’ agents can speak the same language. This is why Model Context Protocol matters.
- Lifecycle: a place to design, test, evaluate, deploy, and iterate agents. Think test suites, scenario simulators, structured feedback loops, and change approvals. A real control plane makes this the default path, not a side project.
If that sounds familiar, it is because it mirrors the last two decades of cloud. We once celebrated raw compute. Then everyone realized scheduling, networking, and security posture were the real differentiators. The same shift is happening for agents.
Why the frontier is not bigger models anymore
Bigger models help in research, yet production value is being throttled by different bottlenecks. Regulated enterprises cannot deploy agents that are invisible black boxes. They need to know which agent took which action, with what input, grounded in what data, and under whose authorization. They need to prove these facts to internal audit, customers, and regulators. If you cannot answer those questions, a smarter agent is not more valuable, it is only more risky. For more on operational durability, see how durable AI agents arrive in real workloads.
That is why control planes are the next competitive tier. They move the conversation from capability ceiling to safety floor and from hero demos to repeatable outcomes. They let teams run many agents in parallel, compare them with shared metrics, retire stale instructions, and roll feature flags to small populations before global release. This is where business value compounds.
MCP is the new lingua franca for agent actions
Model Context Protocol, known as MCP, is becoming the standard way to connect agents to tools and data. The idea is pragmatic. Instead of writing one-off integrations for every system, teams expose resources and tools through an MCP server, and any MCP-capable agent can use them. Anthropic describes MCP as the USB C of AI applications, a single port that fits different accessories. The metaphor works because it is about a reliable plug, not a new type of electricity. If you want to understand the mechanics and why enterprise teams care about permissioning and structured outputs, read the Model Context Protocol documentation.
Salesforce aligned with this reality. Agentforce 3 includes a native MCP client that connects to MCP servers from partners like AWS, Box, Google Cloud, IBM, PayPal, Stripe, Teradata, and Writer. The practical outcome is agent interoperability without custom glue code, governed by the policies companies already use. This fits a broader industry move, including how Windows backs MCP and identity. Major platforms have been signaling support for MCP and building secure registries and consent flows so that agents can tap local files, messaging systems, and enterprise apps with fewer surprises. The pattern is clear. The agent that wins is not the cleverest in isolation, it is the best connected inside a well governed perimeter.
Command centers are the new interface for digital labor
Most teams that tried agents in 2024 ran into the same wall. They could not see what was happening. Debugging meant replaying chats and inspecting prompts. That does not scale. A command center turns that fog into a crisp map. It answers five questions every operator asks:
- What are my agents doing right now, and are they healthy?
- Which tasks cost the most, and why?
- Where does accuracy drop, and what fixes it?
- Which tools are slow or failing, and should we route around them?
- Who approved the latest instruction change, and can I roll it back?
Agentforce 3’s Command Center tackles these head on. It brings session tracing, error and escalation rates, adoption and satisfaction metrics, and the ability to drill into specific moments and outcomes. It pipes signals into the monitoring stack many enterprises already use. This is not the glossy chatbot panel of the past. It is an operations console built to keep digital labor productive and safe. We saw a similar shift as meetings as agent operating systems matured.
Compliance first is not a tagline, it is a design constraint
Compliance first agents do not start with prompts. They start with boundaries. Where is the data stored, which region processes it, which models are allowed, and what is the fallback if a provider is down or out of compliance for a given workload. This is where the control plane earns its name. It can hold traffic rules, model choices, and tool permissions in one place.
The other piece is provability. Audit trails need to show what the agent saw, which tool calls it made, what information left the boundary, and who signed off on this behavior. Public sector customers add a higher bar, which is why authorization levels such as FedRAMP High matter. When your call center agent updates a policy or your finance agent initiates a refund, you must be able to demonstrate that the system was within policy at every step.
A good litmus test is whether an agent platform turns these controls into policy as code that security and risk teams can review. Another is whether red teaming and offline evaluations are built into the lifecycle rather than wedged in after a quiet incident. Compliance first design looks slower at first, then becomes the only way to move fast without breaking trust.
The enterprise playbook for MCP native agents
Many leaders ask how to move from a few promising pilots to a portfolio of agents serving thousands of employees and customers. Here is a concrete plan you can start next quarter.
- Week 0 to 2: pick one business unit and write a charter for three agents with clear objectives. For example, a support triage agent that reduces escalations, a sales research agent that drafts account briefs, and a finance operations agent that reconciles subscriptions. Define success as measurable outcomes such as a percentage reduction in wait time or hours returned to the team.
- Week 2 to 6: expose your systems as MCP servers. Use your integration platform to wrap existing application programming interfaces as MCP resources and tools. Start with read only capabilities and turn on write access only after you have monitoring and approvals in place. Make identity and scope boundaries part of the design from day one.
- Week 4 to 8: instrument the agents. Turn on session tracing, cost meters, and failure codes. Preload a small set of evaluation scenarios that mimic high risk and high volume tasks. Run them daily and treat regressions like build breakers.
- Week 6 to 10: plug into the command center. Create operational dashboards for product owners and wallboards for front line supervisors. Teach teams how to read the signals and when to halt or roll back. Put a named human in the loop for every irreversible action.
- Week 8 to 12: scale carefully. Increase traffic by segment, not by vanity numbers. Keep two models configured for each task so the plane has an alternate runway during outages and pricing spikes. Rotate instructions and prompts behind flags. Record every change.
In parallel, build a three page runbook for each agent: purpose, allowed tools and data, escalation rules, rollback steps, and owner on call. This seems fussy until something goes wrong. Then it is culture saving.
What Agentforce 3 signals about the vendor landscape
Salesforce’s move reframes the market in three ways.
- The control plane is now a product category. Expect more vendors to package observability, governance, and lifecycle tooling as a bundle rather than a scattering of scripts. Buyers will demand this because it reduces risk and speeds audits.
- Interoperability standards are not optional. MCP support will be a checkbox on requests for proposals. Proprietary connectors will still exist, yet they will be a choice rather than a requirement. The path of least resistance will be to publish an MCP server and let customers bring any compliant agent.
- Compliance posture will decide deals. Regional hosting, single tenant options, model choice inside the enterprise boundary, and independent attestations will separate pilots from rollouts. The public sector signal tells every regulated industry what to expect.
Case snapshots that illustrate the point
Consider a healthcare provider that deploys a patient access agent. The agent books follow up visits and routes complex cases to the right teams. Without a control plane, it might overbook, call the wrong system, or leak sensitive data during a tool call. With a control plane, the agent is confined to an approved scheduling server via MCP, every action is traced, and a supervisor has a wallboard that shows escalations and delays. When a regional outage hits, traffic shifts to a secondary model without losing context.
Consider a finance and tax services company during peak season. An administrative chat agent handles a large share of simple intake and document questions. The command center shows resolution rates and flags spikes in escalations. Leaders can drill into the transcripts that caused handoffs, then adjust the instruction set or connect a new document tool through MCP. The team spends less time guessing and more time tuning what matters.
Consider a media company’s retention team. A research agent drafts subscriber offers using data exposed through an MCP server that enforces read only access and strict filtering for sensitive fields. A human signs off on any write operation. The control plane records when the agent stepped outside a confidence band and the dashboard shows whether the change moved renewal rates the next week. The point is not that the agent is brilliant, it is that the process is governable and measurable.
A buyer’s checklist for agent control planes
If you are evaluating platforms over the next quarter, use this short checklist. It is designed to separate surface gloss from operating substance.
- Interoperability: does the platform act as an MCP client and can it register multiple MCP servers with per server policies. Can you publish your own MCP servers without vendor help.
- Observability: does it record session level traces with tool calls, inputs, outputs, and costs. Can you export signals to your existing monitoring tools. Are error classes and escalation reasons standardized and searchable.
- Governance: can you author policies that block or approve classes of actions, not just individual tools. Does it support identity mapping and scoped tokens per server. Can you roll back instruction sets with a click and a record.
- Lifecycle: is there a test center with scenario replay and offline evaluations. Can you flag and canary changes. Can you simulate failures and see how the agent behaves.
- Compliance: does the vendor offer regional hosting, model choice inside your boundary, and audited controls for sensitive workloads. If you work in public sector or healthcare, is the relevant authorization in place.
- Cost to serve: does the platform report all in cost per resolved task, including model usage, tool calls, and observability overhead. Can you attach value to outcomes, not just inputs.
What to watch over the next year
Three developments will matter.
- A real marketplace of MCP servers, curated for security and reliability. This will make it easier to wire agents into complex business systems without custom builds and still keep control.
- Standardized telemetry schemas for agents. The moment observability signals can travel across vendors without translation, multi agent portfolios get much easier to run.
- Reliable service level agreements for agent behavior, not just uptime. Vendors will start quoting guaranteed resolution rates and escalation ceilings for defined tasks, with remedies if they fall short.
The conclusion: control planes unlock the real market
Dreamforce 2025 marked the end of the novelty phase for enterprise agents. With Agentforce 3, Salesforce put a stake in the ground. The next race is to build command centers that make agents observable, to embrace interoperability through MCP, and to treat compliance as a feature, not a footnote. Models will keep improving, and that is good. But the scalable value will come from platforms that make digital labor legible, governable, and interchangeable inside the norms of the enterprise. That is how regulated industries move from careful pilots to confident production. That is how agents stop being a demo and start being a durable advantage.
For more context on the agent stack and how it is reshaping software, see how chat is the new runtime.