Transparent Oceans vs Submarines: AUKUS Races to Adapt
Breakthrough sensing, AI fusion, and swarming autonomy are shrinking the ocean’s shadows and challenging nuclear‑sub stealth. What is real, what is hype, and how AUKUS can adapt fast with Pillar II trials, software reforms, and large undersea drones.

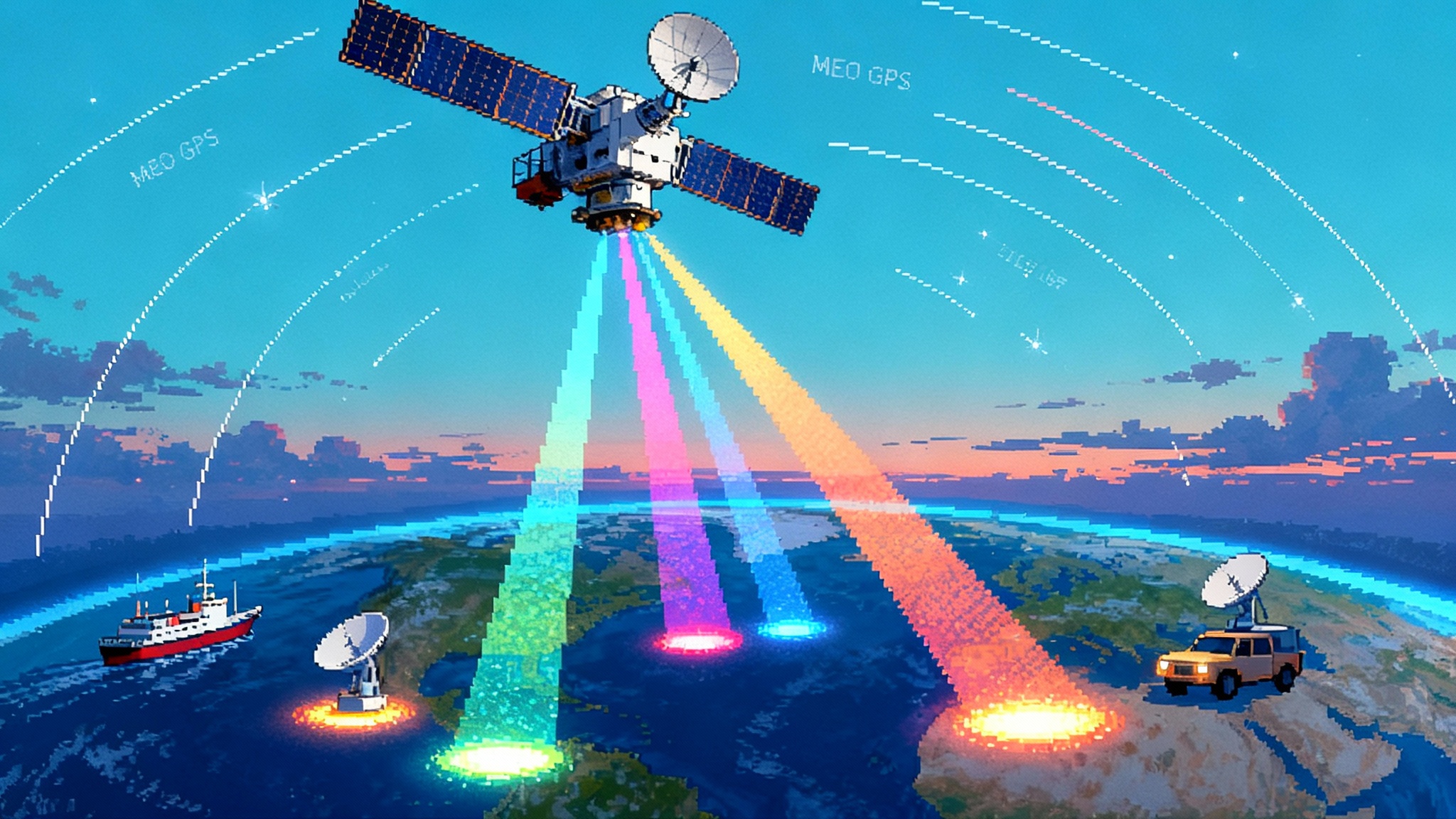
The ocean’s last sanctuary is getting crowded
The oldest assumption in undersea warfare is simple: if a nuclear submarine stays quiet, it stays invisible. That premise is under pressure. Mid‑September reporting on so‑called transparent oceans highlights how quantum magnetometers, distributed acoustic arrays, and AI fusion are beginning to stitch together a picture of what moves under the waves. The claim is not that the deep ocean is suddenly glass. It is that the cost and complexity of wide‑area detection are falling while compute and autonomy proliferate. If that trend holds, the margins that keep big submarines safe could narrow fast, especially near chokepoints and shallow littorals. A debate that once lived in labs and think tanks is now squarely in the policy arena, with mainstream coverage underscoring the risk that exquisite submarines could become easier to find. See this framing in the Guardian analysis on transparent oceans, which captures new urgency around stealth at sea.
Pillar II moves from PowerPoint to saltwater
AUKUS Pillar II is where the three partners turn nervous system into muscle memory: autonomy, AI, quantum, cyber, and advanced sensing pushed into field trials. Two July milestones show the tempo change.
-
On July 16–17, 2025, Japan joined the AUKUS Maritime Big Play autonomy series during Talisman Sabre, testing underwater acoustic communications to task uncrewed systems. Tokyo’s first hands‑on participation under Pillar II signals that interoperability in subsea autonomy is no longer an aspiration; it is an exercise serial with real radios, real wave action, and real friction. The Japanese Ministry of Defense detailed the event and focus on acoustic comms among U.S., U.K., and Australian platforms at Jervis Bay in its Japan MoD Pillar II trials.
-
Also on July 16, 2025, Australia issued one of the first AUKUS export‑control exemptions to an autonomous‑vessel software company. The point was not a single startup; it was the new legal plumbing that lets autonomy code, datasets, and updates flow to partners with fewer delays. This is essential when the “platform” is a fast‑iterating software stack as much as a hull. For context on the broader plan, see our internal look at the AUKUS Pillar II roadmap.
These choices matter because the detection problem is increasingly a software and networks problem. Pillar II aims to move from episodic, bespoke integration toward continuous, software‑defined collaboration where UUVs, USVs, and seabed nodes operate as an upgrading fleet of connected sensors and effectors.
What makes an ocean transparent, really?
Transparency is not a single sensor; it is a mosaic.
Quantum and classical magnetometers
Airborne or seabed systems look for subtle disturbances in Earth’s magnetic field from ferrous hulls, power systems, or even the magnetohydrodynamic wake of a moving submarine. Quantum diamond sensors are hitting impressive sensitivities, and engineers are packaging these gains into platforms with better dynamic range, thermal stability, and noise rejection. Real‑world performance still contends with platform vibration, geomagnetic noise, latitude‑dependent blind zones, and clutter from shipping and seabed infrastructure. The vector is improving.
Distributed acoustic sensing and arrays
Buried hydrophones, seabed nodes, and repurposed telecom fiber using DAS can watch vast swaths of water column. They will never be perfect; ambient noise, marine life, storms, and shipping traffic all generate false positives. Yet with enough density and smart processing, these networks can flag anomalies, cue active sensors, and help maintain a running estimate of uncertain contacts.
Multimodal AI fusion
The real accelerator is not the sensor; it is the stack that fuses magnetics, passive acoustics, wake imagery, and RF or satellite cues into a consistent underwater picture. Confidence grows when multiple weak signals overlap in time and space.
Swarms and persistence
Hundreds of inexpensive autonomous nodes can sit quietly for months, wake up when cued by a passing anomaly, share observations, and hand off tracking to other nodes. Even if each node is only pretty good, the network can be very good.
Put together, these advances do not make the North Pacific a fishbowl in 2025. They do make it easier to deny submarines safe transit in contested littorals, to hold approaches to bases at risk, and to compress the time from first hint to useful track. If you are a large, crewed submarine, that matters.
Counterstealth: the other half of the arms race
Stealth is never static. The same forces making oceans more transparent are also arming submarine designers and operators with counters. Expect the next five years to prioritize:
- Low‑observable signatures across domains: Coatings and structures that damp acoustic scattering; magnetic signature control beyond classic deperming and degaussing; disciplined power‑electronics hygiene to reduce electromagnetic emissions; and thermal management to minimize infrared wakes detectable by satellites in calm seas.
- Wake management: Hull shaping, pump‑jet tuning, and controllable wake‑dampening techniques to reduce persistent turbulence patterns. Research continues on microbubble or polymer injection; the challenge is gaining benefits without creating new signatures.
- Acoustic cloaking and metamaterials: Lab promises abound; operational cloaks remain nascent. More near‑term are hull and propulsor treatments that reduce broadband noise and elastic scattering in frequency bands used by seabed arrays.
- Deception at machine speed: UUV decoys that spoof magnetic, acoustic, and even pressure signatures; expendable noisemakers that decouple a detected wake from the true track; and software‑defined payloads that update mimic profiles as adversary classifiers evolve. See practical playbooks in our guide to undersea autonomy tactics.
- Tactics and water‑space management: More emphasis on environmental exploitation, from riding noisy shipping lanes to hugging internal waves and thermoclines that bend sound, and using seabed terrain to mask against specific array geometries.
Bottom line: counterdetection is still feasible, but it requires continuous adaptation, rapid software updates, and a mixed ecosystem of crewed and uncrewed assets to confuse the picture.
The AUKUS hedge: big autonomy, not just big boats
Australia’s early‑September decision to fund a fleet of Ghost Shark extra‑large autonomous undersea vehicles is the clearest signal that the alliance is hedging. Ghost Shark is not a science project. Its prototypes matured quickly, and Canberra has now committed real money to deliver dozens over roughly five years, with initial operational capability beginning in 2026. The appeal is straightforward: cost per hull orders of magnitude below an SSN, persistent reach, and the ability to take risks in denied waters where a crewed boat cannot. For background, see our primer on Ghost Shark program details.
For AUKUS partners, large AUVs do three things a classic SSN cannot do at scale in the near term:
- Saturate: Persistent pickets around chokepoints and base approaches, seeding waters with quiet sensors and acting as hunters of hostile UUVs.
- Deceive: Act as signatures on demand, complicating an adversary’s all‑source correlation by presenting multiple plausible submarines.
- Strike opportunistically: Carry modular payloads for smart mines, anti‑sub torpedoes, or one‑time kinetic effects with low political risk.
Ghost Shark is not a replacement for a nuclear boat’s speed, payload, or survivability in blue water. It is a complement and a near‑term way to thicken the undersea order of battle while Pillar I submarines arrive over decades.
Timelines: what is real between now and 2030?
- Detection tech: By 2027–2030, expect more countries to field regional gates composed of seabed nodes, repurposed telecom fiber segments, and airborne magnetometer patrols. These will be limited in coverage but potent near ports, chokepoints, and shelf breaks. Blue‑water, open‑ocean continuous tracking of quiet SSNs remains unlikely at scale before 2030 without major classified breakthroughs, but cueing windows will widen.
- Countermeasures: Acoustic and magnetic signature reductions will progress incrementally via software updates to machinery controls and new coatings during maintenance availabilities. Decoys and UUV escorts are near‑term fieldable because they ride on mature commercial autonomy and battery tech.
- Autonomy at scale: The logistics and command‑and‑control of hundreds of undersea nodes is the pacing item. Pillar II’s value is procedural as much as technical: export‑control fixes, shared software repositories, common message sets, and routine combined trials are what make fleet autonomy work in practice.
What the July actions really enable
Japan’s July participation was about more than symbolism; it validated an underwater comms baseline across four navies. That matters because undersea operations are bandwidth‑constrained and latency‑sensitive. Acoustic links are low bitrate and fickle; optical links are short‑range and angle‑dependent. Practicing tasking of UUVs under those limits is the only way to learn how to plan missions that survive real physics.
Australia’s July 16 export‑control exemption is equally structural. If AUKUS wants autonomy to move at software speed, then developers in Perth, Portsmouth, and San Diego need to push and pull code, models, and datasets without month‑long licensing cycles. The exemption is one of the first practical signs that the legal system is catching up to the technical concept of a software‑defined fleet.
Doctrine shifts already underway
AUKUS navies are starting to think of SSNs as motherships and orchestrators rather than lone wolves. In a more transparent ocean, a submarine will:
- Deploy and control UUV screens that scout, deceive, and guard the approaches.
- Use emissions‑controlled playbooks that minimize telltale patterns across acoustic, magnetic, and thermal domains.
- Treat decoy deployment as a routine part of transits through monitored waters.
- Reserve sprint‑and‑drift tactics for moments when environmental conditions give the best cover.
The operational center of gravity moves from perfect invisibility to probabilistic advantage: make it hard to get a confident track, make it costly to sustain it, and inject doubt about which contact is the prize.
Recommendations for the next 3–5 years
Here is a clear, near‑term agenda for the U.S., U.K., and Australia.
Investments
- Field regional detection and deception testbeds: Build instrumented ranges where allied teams can pit transparent‑ocean sensors against submarine countermeasures and share ground‑truthed data. Prioritize one range near a chokepoint, one in a shelf‑break environment, and one deep‑water site.
- Double down on UUVs and decoys: Procure large AUVs like Ghost Shark in meaningful numbers and pair them with families of expendable decoys that mimic acoustic and magnetic signatures. Bake in rapid reprogrammability so mimic profiles evolve as adversary classifiers update.
- Harden autonomy software supply chains: Scale secure CI/CD pipelines and shared repositories under Pillar II so autonomy updates can be pushed fleet‑wide in weeks, not quarters. Expand export‑control exemptions to include trained models and labeled datasets by default, with carve‑outs for restricted payloads.
- Sensor fusion at the edge: Fund onboard AI that filters and compresses raw magnetics and acoustics into low‑bandwidth cues, preserving precious acoustic throughput. Invest in ultra‑low‑power processors and event‑driven architectures for seabed nodes.
- Quieting retrofits: Allocate maintenance windows for targeted upgrades to power electronics, isolation mounts, and propulsor control laws that reduce broadband noise without major hull changes. Treat magnetic hygiene as a continuous task with improved degaussing schedules and portable assessment tools.
Doctrine and training
- Normalize deception: Write decoy employment into standard operating procedures. Train crews to manage UUV escorts and deception timelines under strict EMCON and acoustic limits.
- Plan for contested transits: Use wargames and at‑sea trials to script transits through notional transparent gates, integrating UUV pickets, merchant‑traffic masking, and synchronized timing with friendly surface and air assets.
- Share ground truth: After every combined exercise, release declassified, anonymized datasets across AUKUS to accelerate model training and red‑team analysis. Reward teams that demonstrate cross‑navy, cross‑domain fusion.
- Build red teams that think like data scientists: Train specialists to attack submarine stealth via big‑data correlation, not just traditional sonar tactics. Likewise, train blue teams to spot and break those correlations.
Policy and acquisition
- Make software speed the metric: Tie funding and leadership evaluations to how quickly autonomy updates, sensor‑fusion models, and countermeasure profiles move from lab to fleet. Publish quarterly time‑to‑fleet dashboards across Pillar II.
- Expand legal plumbing: Keep broadening the July exemption model so allied SMEs can participate without drowning in compliance. Create standing, pre‑approved data licenses for non‑weapon autonomy components.
- Keep two external pathways open: One for exquisite SSN stealth improvements that will take years, and another for rapid, iterative UUV, USV, and seabed‑network deployments that deliver capability every quarter.
The race is on, but it is not over
Transparent‑ocean narratives can tempt fatalism. The reality is more nuanced. Detection is getting better, especially in places that matter. Stealth is also getting better, and deception can turn an adversary’s data lake into a swamp. AUKUS is acting like an alliance that understands both truths: it is pushing autonomy and sensing into the water, unblocking the legal pipes to share software, and hedging with large uncrewed undersea systems that will fight differently.
The task for the next five years is clear: test relentlessly, share ruthlessly, update continuously. If the ocean is becoming more transparent, victory goes to the team that adapts faster, not the one that waits for perfect invisibility to return.