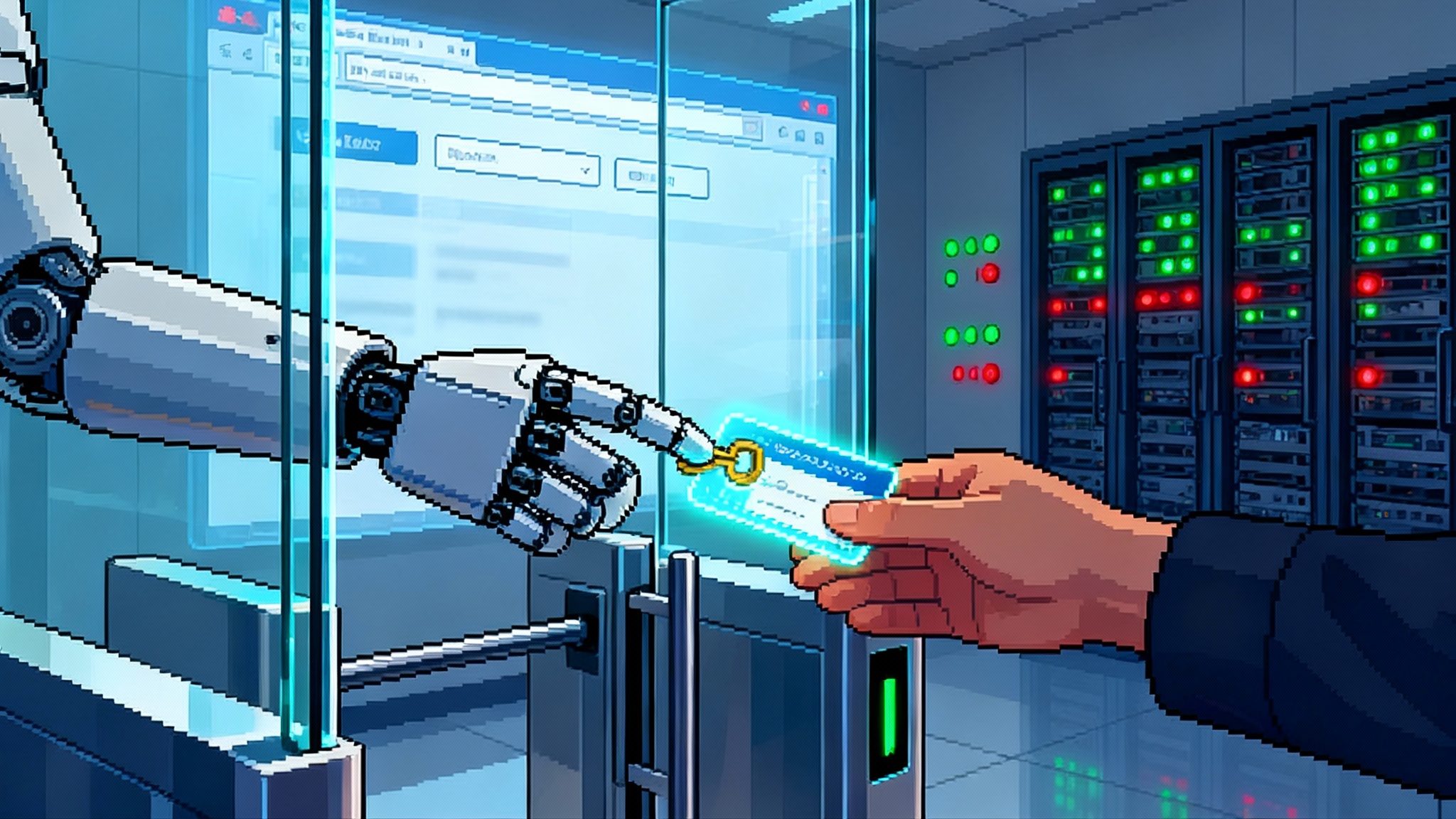
The Credential Broker Layer For Safe AI Browser Agents
A new middleware tier is forming between agents and the web. Driven by passkeys, zero-day churn, and prompt-injection research, credential brokers will gate logins and risky clicks. Here is how it becomes the 2026 enterprise stack.
Breaking: Security turns into product, right in the agent’s path
Enterprises are discovering a simple truth. If an artificial intelligence agent can drive a browser, it can spend money, move data, and change configurations at machine speed. The same capability that makes Gemini, Claude, and ChatGPT-style agents useful also makes them dangerous. After a year of high-profile browser vulnerabilities, steady prompt-injection findings, and a new wave of password-manager features, a distinct product category is coming into focus. Call it the credential broker layer for AI browser agents.
This layer sits between the agent and everything the agent touches online. It holds the keys, decides which locks an agent is allowed to open, and asks a human when a door looks suspicious. By 2026, most large companies will assemble this layer from tools they already own and from a set of new products now racing to market. The rise of Gemini 2.5 browser-native agents is pushing this from theory to practice.
Why now
Three forces are converging.
-
Browser exposure: Attackers continue to aim at the browser, because it is where identity, secrets, and critical workflows live. A single remote code execution or cross-origin bypass can convert an agent from helpful assistant into autonomous intruder. Even without a new exploit, simple session stealing or extension abuse can yield the same outcome.
-
Agent misdirection: Prompt injection research keeps showing that agents obey convincing lies embedded in web pages, documents, and emails. That means an agent can be tricked into disclosing secrets, changing system settings, or navigating to malicious flows, all while thinking it is helping.
-
Credential product push: Password managers and identity providers are leaning into automation, passkeys, and granular sharing. This is not cosmetic. It is the substrate for letting software do work while keeping secrets fenced. The move from stored passwords to hardware-backed passkeys creates a foundation for controlled delegation and precise scopes. See the FIDO Alliance passkeys overview for the underlying model.
Put these together and you get a clear need: a broker that can say yes or no to each agent intention, and that can carry the right secret only when that yes is earned.
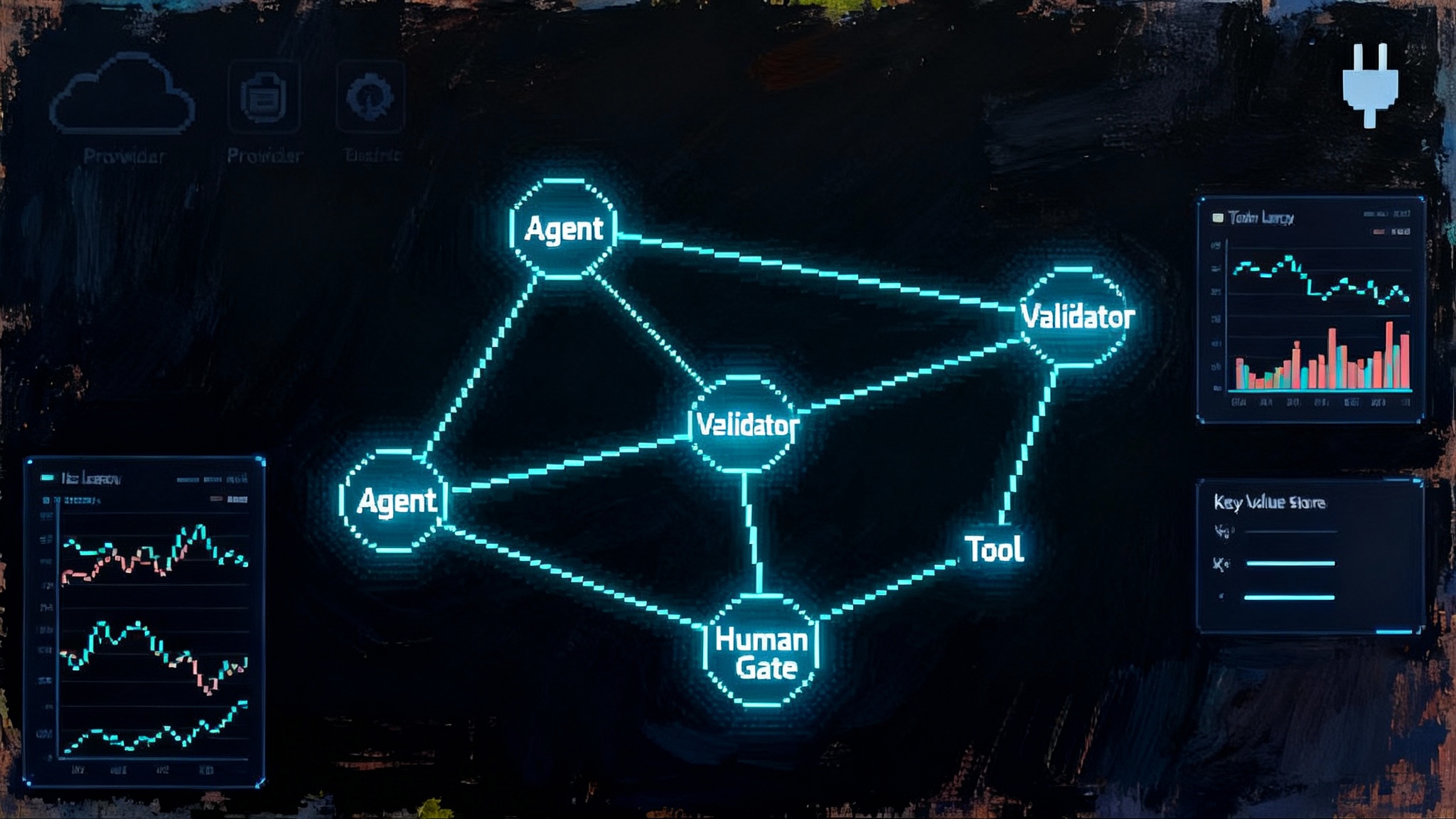
Define the credential broker layer
Think of a hotel concierge with a ring of keys. The concierge does not hand the ring to a guest. They escort the guest to the right door, use a single key for that door, and log the time. The credential broker does the same for an agent. It intermediates:
- Which identity to present in which domain
- Which credential or passkey to use
- Which scope of access is permitted for this task
- Which actions cross a risk threshold and require human approval
- Which session is properly attested as trustworthy
This is not a single product yet. It is a stack. It starts with secrets storage and ends with action approvals, with policy in between. In 2026 this stack will likely have four pillars.
The four pillars of the 2026 agent stack
1) Human-in-the-loop approvals at the right moments
Agents are fast, but some actions must be slow by design. Money movement above a threshold. New administrator creation. Data export from regulated systems. The broker’s job is to intercept these steps and change the tempo.
-
Just-in-time prompts: When the agent is about to submit a form that triggers a wire transfer, the broker pauses the browser, shows a snapshot of the page, highlights the amount and destination, and requests a human tap to continue or deny. The pause is not optional. The agent cannot override it.
-
Safe summaries: Before the tap, the broker summarizes the action in plain language, including the origin, destination, and net effect. If the agent reached the action through a convoluted path, the broker shows the path.
-
Out-of-band channel: The approval flows through a separate channel, such as a mobile authenticator or a desktop notification controlled by the security team, to reduce spoofing risk.
2) Least-privilege scopes bound to a task
Agents should not inherit the operator’s all-powerful access. They should borrow only what they need, only while they need it, and only for the specific domain involved.
-
Task-scoped identities: The broker issues a short-lived credential or passkey assertion tied to a single domain and a specific purpose. The agent never sees the underlying secret. It only gets a one-time assertion or a delegated handle.
-
Per-site fences: Access to billing in vendor A does not imply access to billing in vendor B. Even within vendor A, the scope can exclude dangerous controls like user deletion unless explicitly needed.
-
Automatic revocation: When the task ends or time expires, the broker revokes tokens, clears cookies, and tears down the logical session. Logs tell you what was used and why.
3) Attested browser sessions
If you cannot trust the environment, you cannot trust the action. The broker should only release sensitive assertions into a session that proves it is unmodified and policy-compliant.
-
Hardware-rooted checks: The browser session presents proof that it runs on a device with a trusted platform module or secure enclave, with approved extensions, on an up-to-date build, and with anti-tampering active.
-
Isolation by design: High-risk flows launch inside a hardened profile or container with strict network egress controls and clipboard policy. The agent can navigate and click, but cannot exfiltrate.
-
Recorded provenance: Every delegated credential use is tied to an attestation record. If something leaks, you can trace the where and when.
4) Operating system level permission brokers
The best place to enforce controls is below the browser, where it is hard for web content to interfere.
-
Centralized prompts: A system service, not the site, asks for consent when the agent tries to access the camera, filesystem, or keychain. The system prompt is unspoofable and policy-aware.
-
Event-level policy: The broker can deny clipboard reads from sensitive windows, block unknown downloads, and prevent simulated keystrokes into protected apps.
-
Endpoint-grade telemetry: The same service emits signals to endpoint detection and response tools. EDR stands for endpoint detection and response. The goal is to catch chains of actions that look benign individually but risky together.
How it works in practice
Picture a finance agent tasked with refunding a suspicious charge in a vendor dashboard.
- The operator tells the agent to investigate and refund if the customer is correct.
- The agent launches a controlled browser profile. The credential broker verifies attestation and policy. Extensions are whitelisted. Recording begins.
- When the agent hits the vendor login page, it requests a credential. The broker matches the domain, the task, and policy, then injects a passkey assertion without revealing the secret. Cookies land in the hardened profile only.
- The agent navigates to the billing section. It prepares a refund. The refund exceeds the threshold. The broker interrupts, captures the rendered page, and sends an approval to the operator’s device. The message says: “Refund 1,240 dollars to customer ABC for invoice 7735 in VendorCo. Path: Login, Billing, Orders, Refund. Approve for 45 seconds.”
- The operator taps approve. The broker releases the click and logs the action. When the task ends, the profile and tokens are destroyed.
At no point did the agent get a reusable password or an unbounded identity. At every sensitive step, the system forced a check that a human could understand.
The emerging control plane: who plays where
This new layer draws products from three familiar camps.
-
Password managers: Tools like 1Password, Dashlane, Bitwarden, and platform vaults such as Apple’s iCloud Keychain are moving beyond storage. They offer passkey orchestration, item sharing with granular permissions, and secure autofill automation. They are the natural custodians of secrets and the first line of domain matching and injection control.
-
Identity providers: Identity provider platforms like Okta and Microsoft Entra can issue scoped tokens, enforce conditional access by device posture, and deliver approval prompts through authenticators. They hold policy, groups, and context. They are the natural source of least-privilege and just-in-time identity.
-
Endpoint security: Endpoint detection and response vendors such as CrowdStrike, Microsoft Defender for Endpoint, and SentinelOne sit at the operating system layer. They can attest the host state, enforce application control, and stream telemetry. They are the natural place to certify that an agent session is trustworthy.
The control plane emerges where these overlap. In some shops the password manager will surface the approval and passkeys, while the identity provider binds the session to the right role and the endpoint tool signs the attestation. In others, the identity provider takes the lead and the password manager becomes a service plugin. Market structure will vary, but the function will look consistent. This mirrors the enterprise agent stack unification already underway.
The technical building blocks
-
Passkeys and platform authenticators: Modern browsers and devices support device-bound credentials that never expose a shared secret. That allows a broker to authorize without revealing a password to an agent.
-
Browser automation interfaces: Agents drive browsers through documented protocols that separate navigation from the internals of the page. A practical primer is the WebDriver BiDi overview. A broker can sit between the command stream and the browser, pausing or denying high-risk steps. This aligns with frameworks setting the agent runtime standard.
-
Attestation: Hardware exposes identity and state signals, from trusted platform module quotes to secure enclave measurements. The broker checks these before releasing sensitive assertions.
-
Zero trust policy engines: Fine-grained decisions take into account user, device posture, network, time, and task. Zero trust means no implicit trust, only continuous verification using least privilege.
-
System permission frameworks: Operating systems already have prompts for camera, microphone, screen recording, and filesystem. Agent control should extend through the same pipes so the rules are consistent and unspoofable.
Handling prompt injection without hand waving
Prompt injection is not solved by a better prompt. It is a supply chain problem where untrusted content can carry commands that the agent tries to follow.
A credential broker reduces blast radius by changing what an injected instruction can do.
-
Secret starvation: Even if an instruction convinces the agent to fetch secrets, the agent does not have them. The broker only releases a bounded assertion for the current site and task.
-
Action tripwires: Dangerous actions route through human approval. An injection may prepare the action, but it cannot submit without an external tap.
-
Context hygiene: The broker can scrub or compartmentalize context. It can prevent content from one domain from informing actions in another domain unless specifically allowed by policy.
-
Provenance-aware rules: If the agent came from a low trust source, the broker can clamp down scopes and require more approvals. Risk flows downhill.
Failure modes you must design for
-
Shadow credentials: If teams keep local spreadsheets of passwords for automations, the broker will be bypassed. Inventory and migrate these secrets. Make the broker the easiest path.
-
Prompt fatigue: If every click requests approval, humans will rubber-stamp. Identify the top ten risky actions in your environment and bind approvals to those. Start small and tighten over time.
-
Attestation gaps: If your broker believes unverifiable claims about the device state, a compromised host will look clean. Pair attestation with independent endpoint signals and version enforcement.
-
Browser drift: Extensions and experimental flags can quietly change web behavior. Lock approved profiles, sign extensions, and watch for unauthorized flags.
-
Data puddling: Logs and session recordings are themselves sensitive. Classify and protect them. Redact secrets in captures automatically.
Build or buy
Some companies will assemble the layer from existing tools. Others will buy a unified product. Use these tests to decide.
- Can your password manager inject passkeys and passwords only into verified sessions, and can it refuse to reveal raw secrets to agents?
- Can your identity provider issue per-task, per-domain delegations with time limits and kill switches, and can it drive human approvals out of band?
- Can your endpoint tools assert device posture and squash risky actions at the operating system level, not just after the fact?
- Can your browser management enforce hardened profiles for agents and record provable provenance for each sensitive action?
If you can do all four with the tools you have, integrate and proceed. If not, look for broker products that integrate natively with your identity provider, password manager, and endpoint suite. You want policy in one place and enforcement in three.
A 12-week plan to get to a brokered agent pilot
Week 1 to 2: Inventory. Catalog which workflows your agents perform in the browser. List the secrets and sites. Rank actions by business impact.
Week 3 to 4: Harden the browser. Create dedicated agent profiles with signed extensions, controlled flags, and restricted network egress. Turn on recording of sensitive flows in a privacy-conscious way.
Week 5 to 6: Move secrets. Migrate credentials for these workflows into a centralized password manager with passkey support. Disable local caches and plaintext stores.
Week 7 to 8: Add identity scopes. Work with your identity provider to issue short-lived tokens or passkey delegations for each domain. Wire conditional access to device posture.
Week 9 to 10: Wire approvals. Define the top ten high-risk actions. Implement mandatory human-in-the-loop prompts that show a rendered snapshot and a clear summary.
Week 11 to 12: Test prompt injection. Seed an internal site with realistic attacks. Observe how the brokered stack responds. Tune policies until the agent can continue useful work while risk is contained.
What to ask vendors this quarter
- Show me a complete refund flow with an agent where your product injects a passkey assertion without revealing a password to the agent, and where a human must approve the final submit.
- Demonstrate denial. Trigger a policy that blocks the action and show me the agent’s error. I want to see the exact user message and the audit trail.
- Prove attestation. Tamper with the browser and device. Show that the broker refuses to release credentials until the posture is clean.
- Integrate identity. Swap users and roles mid-flow. Show that scopes change immediately and that stale tokens die.
- Emit signals. Stream events into our security information and event management system. We want to correlate approvals, clicks, and network egress.
How this reshapes roles and budgets
Security teams become product managers for the agent runtime. Identity teams become publishers of least-privilege roles and short-lived delegations. Platform teams own hardened browser distributions and automation interfaces. Procurement pushes vendors to plug into a shared control plane rather than sell overlapping islands.
Budgets shift from passive detection to active intermediation. Expect spend to move toward password managers that do policy, identity providers that do per-task delegation, and endpoint suites that do attestation and permission enforcement. The reward is not a new dashboard. It is the confidence to let agents work without waking the incident team every night.
The bottom line
Agents will keep getting better at reading the web and driving the browser. Attacks will keep adapting. The winning pattern is simple: never hand an agent the key ring. Instead, interpose a broker that understands identity, verifies the environment, and slows down the right moments for a human to decide.
If you build toward human-in-the-loop approvals, least-privilege scopes, attested sessions, and operating system level permission brokers, you will have the backbone of the 2026 enterprise agent stack. The market will sort out the packaging. Your job is to shape the control points now so that when the wrappers arrive, they snap cleanly into place.
Get the approvals right. Fence the scopes. Prove the session. Enforce at the operating system. Then give your agents real work and sleep well.